Introduction to Ethical Hacking
Ethical hacking might sound like an oxymoron, but it's a crucial part
of cybersecurity. Imagine it as being a superhero in the digital world. These
professionals use their powers for good, helping to protect us from the bad
guys. Unlike malicious hackers, ethical hackers have permission to break into
systems. But why? To find weaknesses before the bad guys do.
Think of your home's security system. You'd want to find any weak spots
before a burglar does, right? Ethical hackers do the same with computer
systems. They search for weak points that could let hackers in. Then, they help
fix these issues, making the system safer for everyone.
Getting into ethical hacking isn't just about being good with
computers. It's about thinking like a hacker, but acting like a hero. Ethical
hackers use many of the same tools as malicious hackers. The big difference?
Their intent. They aim to improve security, not break it.
Skills and Tools
Critical Thinking: Seeing the big security picture.
Technical Skills: Understanding how systems and
networks work.
Problem-Solving: Finding and fixing security issues.
Becoming an ethical hacker takes time and dedication. But for those
passionate about cybersecurity, it's a rewarding path. You get to be the
digital world's hero, protecting people and companies from cyber threats.
The Role of Ethical Hacking in Cybersecurity
In the vast ocean of the internet, ethical hackers are the lifeguards.
They play a vital role in cybersecurity, acting as the first line of defense
against cyber threats. Let's explore how they make the digital world safer for
everyone.
Identifying Vulnerabilities
One of the main tasks of ethical hackers is to find vulnerabilities.
These are like the hidden backdoors that bad hackers try to exploit. By finding
and fixing these first, ethical hackers help prevent potential attacks.
Strengthening Security
After finding vulnerabilities, the next step is to strengthen the
system's security. This might involve installing updates, patches, or making
changes to the system's configuration. It's like adding extra locks to your
doors after finding out they're easy to pick.
Preventing Data Breaches
Data breaches can cost companies millions and erode public trust.
Ethical hackers work hard to prevent these. By testing the system's defenses,
they can ensure that sensitive data stays safe. It's a bit like testing the
strength of a dam before the storm hits.
Without ethical hackers, the cyber world would be a much more dangerous
place. They help keep our data safe, protect our privacy, and ensure that
businesses can thrive in a secure digital environment. So next time you log in,
remember the unseen heroes keeping your digital life secure.
Tool #20: Wireshark - Network Packet Analysis
Imagine being able to see everything sent over your network, like
texts, emails, and website visits. That's what Wireshark lets you do. It's a
tool that ethical hackers use to catch bad guys in the act.
Key Features
Packet Capture: Grabs data traveling over your network.
Live Data Analysis: View and analyze network traffic in
real-time.
Deep Inspection: Dive deep into network packets to
see what's hidden inside.
Using Wireshark, ethical hackers can spot suspicious activities. It
could be someone trying to sneak into your network or a program sending data it
shouldn't. By catching these early, they keep networks safe from attackers.
Tool #19: Nexpose - Vulnerability Management
Imagine your computer is a castle. Nexpose helps make sure the walls
are strong, and the gates are locked tight. It's a tool that looks around your
digital castle for any weak spots.
How It Works
Scans Your Network: Finds where attackers could break
in.
Risks Analysis: Shows how serious each weak spot is.
Solution Proposals: Gives you ways to fix the problems.
Nexpose is like having a security guard walking around, checking for
open windows or doors left unlocked. It's constantly looking for new
vulnerabilities, keeping your digital castle safe from attackers.
Tool #18: Burp Suite - Web Application Security Testing
Burp Suite is like a Swiss Army knife for web security experts. It
packs a bunch of tools in one, making it easier to test web applications for
security holes.
What You Can Do With It
Scan for Vulnerabilities: Automatically find security
weaknesses in your web apps.
Test Session Handling: Check if users can stay logged in
securely.
Analyze Requests and Responses: Look at the data going back
and forth between the user and the site.
Burp Suite can help you catch security issues before the bad guys do. It's a must-have for keeping web applications safe.
Tool #17: Nessus - Vulnerability Scanner
Nessus is like having a cyber detective on your team. It digs through your network, looking for clues that could lead to security issues.
Why It's Awesome
Wide Reach: Scans for thousands of vulnerabilities across your systems.
Easy to Use: You don't need to be a tech wizard to run scans.
Up-to-Date: Always learning about the latest
security threats.
With Nessus, you can find and fix security risks before they become a problem. It's trusted by loads of organizations to keep their data safe.
Tool #16: Aircrack-ng - Wi-Fi Network Security
Aircrack-ng is like a magic wand for Wi-Fi security. It helps ethical hackers test
network security and find weaknesses. Think of it as a tool that can crack
Wi-Fi passwords to test how strong they are.
What Makes It Special
Key Recovery: Can recover network keys once enough data is captured.
Monitoring: Keeps an eye on network traffic to spot suspicious activities.
Testing Network Strength: Helps you test how easy or hard it
is to crack your Wi-Fi security.
With Aircrack-ng, you can make sure your Wi-Fi is as tough as it can be. It's like putting your network through boot camp to toughen it up!
Tool #15: Nmap - Network Discovery and Security Auditing
Nmap stands for Network Mapper, and it's like having a digital map of
the entire internet. Ethical hackers
use it to find devices connected to a network and figure out what holes or
vulnerabilities are present.
Why Everyone Loves It
Discovering Devices: Finds every device connected to a
network.
Identifying Services: Tells you what services each device
is running.
Security Audits: Helps check networks for known vulnerabilities.
Using Nmap, ethical hackers can get a bird's-eye view of a network's security posture. It's like having X-ray vision for networks.
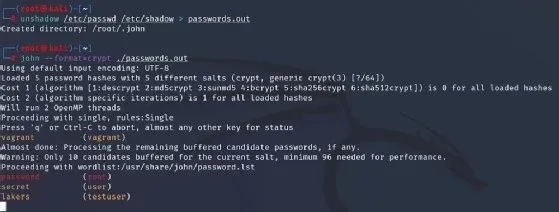
Tool #14: John the Ripper - Password Cracking
John the Ripper is a fast and versatile password cracking tool. It's designed to help ethical hackers find weak passwords within a system.
Why It's Useful
Multiple Encryption Support: Works with many types of encryptions,
making it very flexible.
Speed: Known for its fast-cracking speed.
Customization: Allows users to tailor attacks for specific needs.
John the Ripper excels in cracking simple passwords quickly. However, it can also tackle more complex passwords with the right techniques. By identifying weak passwords, organizations can enhance their security posture significantly. Remember, a secure password is a strong line of defense.
Tool #13: Acunetix - Website Vulnerability Scanner
Acunetix is a powerful tool for detecting vulnerabilities in websites and web applications. It scans for over 4500 types of weaknesses.
Key Benefits
Comprehensive Scanning: Checks for SQL injections, XSS, and
other vulnerabilities.
Automated: Quickly scans without needing manual input.
Detailed Reports: Provides in-depth reports to help
fix issues.
With Acunetix, businesses can protect themselves against a wide range of web threats. It's like having a digital watchdog guarding your site. By closing security gaps, companies can safeguard their data and maintain their reputation. Stay vigilant and keep your web presence secure.
Tool #12 to #7: From Hashcat to Nikto - Advanced Security Tools
Let's dive into some advanced tools that ethical hackers use to protect
our digital world.
Tool #12: Hashcat - Password Recovery
Hashcat is a powerful tool for recovering lost passwords. It's super-fast
and supports many encryption types. Here's why hackers love it:
Speed: It’s known as the fastest password cracking tool.
Versatile: Works with lots of encryption types, from simple to complex.
User-Friendly: Even beginners can learn to use it effectively.
Tool #11: W3af - Web Application Attack and Audit Framework
W3af scans for vulnerabilities in web applications. It's like a
check-up to find where a website might get sick from hackers.
Scans Deep: Looks into every corner of a website for weak spots.
Customizable: Hackers can adjust it to focus on specific areas.
Detailed Reports: Shows exactly where and what the
problems are.
Tool #10: OWASP ZAP - The Zed Attack Proxy
ZAP is a popular choice for finding web app vulnerabilities. It's
open-source and user-friendly.
Automated Scans: Quickly finds weaknesses without
much work.
Easy to Use: Great for beginners but powerful enough for pros.
Active Community: Lots of support and updates from
users worldwide.
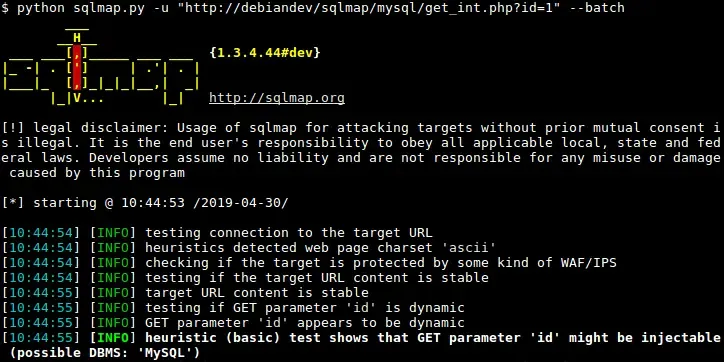
Tool #9: SQLmap - Automated SQL Injection Tool
SQLmap automates the process of detecting and exploiting SQL injection
flaws. It makes databases say "oops."
Powerful: Can take over database servers.
Flexible: Works with different database systems.
Easy to Use: Hackers can start with basic knowledge.
Tool #8: THC Hydra - Network Logon Cracker
THC Hydra is great for testing network security. It cracks passwords to
see if your logins are strong enough.
Fast: Quickly tests multiple accounts.
Supports Many Protocols: Can attack many types of logins.
Widely Used: Popular in the ethical hacking community.
Tool #7: Nikto - Web Server Scanner
Nikto scans for vulnerabilities in web servers. It’s like a health
inspector but for websites.
Comprehensive: Checks for thousands of potential issues.
Up-to-Date: Constantly updated with the latest threat info.
Open Source: Free to use for anyone looking to boost their security.
Top 6 Ethical Hacking Tools: Maltego to Metasploit
Moving on to the cream of the crop, these are the tools that top
ethical hackers swear by.
Tool #6: Maltego - Digital Forensics
Maltego is all about gathering information. It helps hackers understand
the target better.
Rich Data: Collects huge amounts of info from open sources.
Visual Maps: Shows connections in easy-to-understand charts.
Customizable: Hackers can tweak it to fit their specific needs.
Tool #5: AppScan - Application Security
AppScan focuses on making apps safer. It scans for weaknesses that
hackers might exploit.
Deep Scans: Looks into every line of code for hidden bugs.
User-Friendly: Designed for both newbies and pros.
Compliance Help: Makes sure apps meet security
standards.
Tool #4: Retina - Vulnerability Scanner
Retina scans networks to find vulnerabilities. It's like a detective
searching for clues on how hackers might get in.
Fast: Quickly checks big networks without slowing down.
Comprehensive: Finds a wide range of potential security issues.
Easy to Use: Simple for anyone to start scanning.
Tool #3: Kali Linux - Ethical Hacking OS
Kali Linux is an operating system made just for ethical hacking. It
comes packed with tools for testing security.
All-in-One: Has tons of tools ethical hackers need.
Free: Open source and available to anyone.
Community Support: A big community helps with problems.
Tool #2: Snort - Network Intrusion Detection
Snort keeps an eye on network traffic. It looks for signs of hackers
trying to sneak in.
Real-Time Alerts: Warns you the moment it spots
trouble.
Flexible: Can adapt to many types of networks.
Widely Used: Trusted by companies all over the world.
Tool #1: Metasploit - Penetration Testing Framework
Metasploit is the top choice for testing a system's defenses. It’s like
a fire drill to see how well a system stands up to an attack.
Powerful: Can test systems in many complex ways.
Versatile: Works for testing networks, software, and more.
Large Community: Lots of experts contribute to making
it better.
Conclusion: The Future of Ethical Hacking
As the internet grows, so does the need for ethical hacking. It's a
field that's becoming more important every day. Let's look at what the future
might hold for ethical hacking. More Demand for Ethical Hackers. Companies and
governments will need more ethical hackers. They help keep data safe from bad
guys. So, expect to see more jobs in this area.
New Tools and Techniques
Just like in a spy movie, ethical hackers will get new gadgets and
tools. These will help them stay one step ahead of cybercriminals.
Learning and Sharing Knowledge
More people will learn about ethical hacking. Schools might even start
teaching it. Plus, hackers will share what they know, making the internet a
safer place.
So, what's the bottom line? The future of ethical hacking looks bright. As technology advances, so will the ways we protect it. Ethical hackers will be the heroes, fighting to keep our digital world safe. Remember, in the battle against cybercrime, knowledge is our best weapon. Let's get ready for an exciting future.